Ethical Hacking Ppt
Free Ethical Hacking PowerPoint Templates. Free Technology PowerPoint Template. Science and information technology are making progress with every passing day. PowerPoint Templates Hacker. 93% of Fortune 1000 companies use our PowerPoint Products Standing Ovation Award Winner: Best PowerPoint Template Collection Network Solutions protects. Introduction Ethical hacking also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use,but with one major difference that Ethical hacking is legal. Ethical Hacking Independent computer security Professionals breaking into the computer systems. Neither damage the target systems nor steal information. Evaluate target systems security and report back to owners about the bugs found. An Ethical Hacker exposes vulnerabilities in software to help business owners fix those security holes before a malicious hacker discovers them. In this ethical hacker eBook, you learn all about Ethical hacking with loads of live hacking examples to make the subject matter clear. Inside this Ethical Hacking Tutorial PDF Section 1- Introduction.
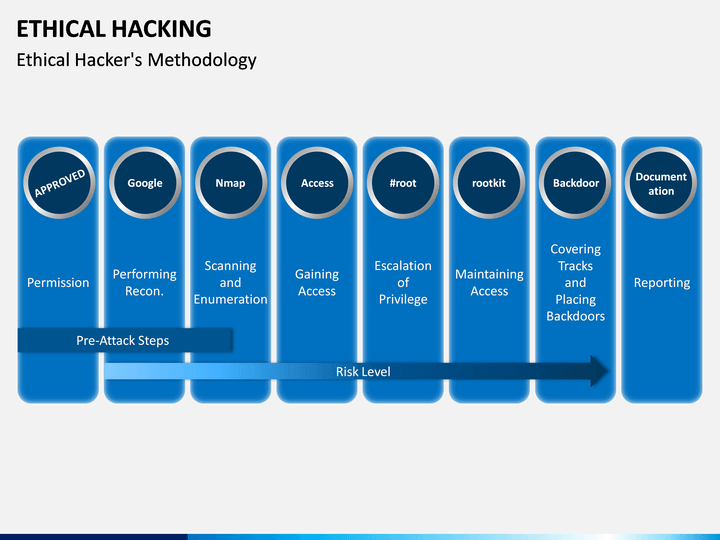
Hacking significantly affects the development of systems and networks. This is especially the case of systems and networks of organizations where sensitive or confidential information are used on a regular basis. Organizations must find solutions and measures to protect information technology assets. In this endeavor, organizations can use ethical hacking. Ethical hacking is a hacking role that business organizations can exploit for security purposes. Ethical hacking presents advantages to increase the capabilities of organizations to protect their IT and information assets. Ethical hacking sheds a positive light on hacking. Nonetheless, any organization that implements ethical hacking must consider the potential negative impacts and issues arising from the practice.
This article discusses ethical hacking and the code of ethics of ethical hacking, the legal risks, and professional issues involved in ethical hacking.
What is ethical hacking?
Ethical hacking is the intentional penetration of a system or network for the purpose of discovering vulnerabilities and evaluating the security of the system or network. The organization hires the ethical hacker to hack the organization’s system or network. The ethical hacker is responsible for discovering the security issues and vulnerabilities of the system or network. The business organization allows the ethical hacker to make the necessary steps or actions to do his job.
The ethical hacker is typically an outsider hired to hack the organization’s system. Hiring an outsider is usually preferred because it ensures that the ethical hacker uses an organic and natural approach from scratch. This simulates possible external hacking attacks.
Ethical Hacking Pros and Cons
The advantage of ethical hacking is that it supports business efforts to gain more comprehensive knowledge about the organization’s IT security. Through ethical hacking, the organization identifies security vulnerabilities and risks. This knowledge helps improve organizational efforts to strengthen security measures.
However, the main disadvantage of ethical hacking is that it presents risks of information disclosure. As an outsider, the ethical hacker could intentionally or unintentionally disclose the company’s confidential information to other parties.
Legal Risks of Ethical Hacking
The legal risks of ethical hacking include lawsuits due to disclosure of personal or confidential information. Such disclosure can lead to a legal battle involving the organization and the ethical hacker. It is very easy for ethical hacking to result in a legal battle if it is not performed properly. It is also possible for the ethical hacker to commit errors to the point that the organization’s profitability is negatively affected.
In such a case, the organization could sue the ethical hacker for failing to perform properly. The ethical hacker could be at legal risk if proper care and precaution are not seriously taken. To address these legal issues, it is imperative for the ethical hacker to always perform his job defensively to minimize compromising the client’s system or network. Defensive performance emphasizes prevention and extra caution in ethical hacking.
Ethical Hacking Ppt For Seminars
Ethical Hacking Professional Issues
The professional issues of ethical hacking include possible ineffective performance on the job. Ethical hacking may be limited by the sensitivity of information involved in the client organization. Clients tend to impose requirements and limits on the activities of the ethical hacker.
For the ethical hacker to perform properly, access to the entire system or network might be needed. Because of the need for professionalism, the ethical hacker must not violate the limits imposed by the client so that professional issues are minimized.
Designing the Ethical Hacking Code of Ethics or Conduct
Codes of ethics or conduct for ethical hacking are focused on the duties, responsibilities and limits of the ethical hacker in doing his job. The ethical hacker makes sure that the client’s system or network is properly evaluated for security issues and vulnerabilities. Because of the nature of ethical hacking, it is not surprising that the ethical hacker could come across sensitive, personal, confidential or proprietary information. In this regard, the ethical hacking code of ethics should guide the actions of the ethical hacker in handling such information. The code of ethics must focus on the protection of the client’s system or network, as well as the effectiveness of the ethical hacker in doing his job.
Code of Ethics for Ethical Hackers (An Example)
- Before performing any ethical hacking, ensure that you know and understand the nature and characteristics of the client organization’s business, system and network. This will guide you in handling sensitive, confidential or proprietary information you might encounter during the ethical hacking.
- Before and during ethical hacking, determine the sensitivity or confidentiality of the information involved. This should ensure that you do not violate laws, rules and regulations in handling sensitive personal, financial or proprietary information.
- During and after ethical hacking, maintain transparency with the client. Communicate all relevant information you found while ethically hacking the client’s system or network. Transparency ensures that the client knows what is going on. Transparency enables the client to take necessary actions for security of the system or network.
- While performing ethical hacking, do not go beyond the limits set by the client. In ethical hacking, it is possible for you to have access beyond the target areas that the client signed up for. Stay within the target areas of the system or network specified in the work agreement. Do not go to other areas or components of the system or network that are not specified in the agreement. Minimize exposure of sensitive information. Increase your trustworthiness and reliability as an ethical hacker. Ensure the overall effectiveness of the ethical hacking activity.
- After performing ethical hacking, never disclose client information to other parties. Ensure the protection of the client. Ethical hacking is done for the security of the client’s system or network. Disclosure of the client’s confidential information renders ethical hacking ineffective. Private information must be kept private, and confidential information must be kept confidential.
Ethical Hacking Ppt
References
Ethical Hacking Course Pdf
- Bansal, A., & Arora, M. (2012). Ethical Hacking and Social Security. Radix International Journal of Research in Social Science, 1(11), 1-16.
- Engebretson, P. (2013). The basics of hacking and penetration testing: ethical hacking and penetration testing made easy. Elsevier.
- Sheoran, P., & Singh, S. (2014). Applications of Ethical Hacking. International Journal of Enhanced Research in Science Technology & Engineering, 3(5), 112-114.
- Spafford, E. (1997). Are computer hacker break-ins ethical? National Institute of Standards and Technology, Computer Security Resource Center.
- Suryawanshi, V., Mavkar, R., & Yadav, K. (2012). Ethical Implications to Hack & Issues in Information Security. Advances in Computational Sciences & Technology, 5(2), 457-460.
